Simulated Phishing Exposes the True Cyber Vulnerability of Businesses
There is no shortage of cyber threats in 2020. With infectious ransomware attacks shutting businesses out of their systems, spyware stealing industrial secrets and phishing scams frauding organisations out of their money, businesses are struggling to find the right solutions to keep themselves protected.
Yet there is one common factor that ties all these threats together: their reliance on human error. According to research from IBM, human error is a leading cause of over 90% of breaches - and is involved in some manner in almost every case of virus and malware infections. In addition, cyber attacks like phishing rely entirely on human misjudgement.
Many organisations are still oblivious to the threat that human error poses. Business leaders may believe that their company is too small or insignificant to be targeted - or that their employees have enough common sense not to fall for scams. Without the proper precautions, however, cyber breaches are inevitable: a third of small businesses faced a breach or attack in 2018.
In order for businesses to take the right precautionary action to protect themselves from breaches, senior management has to first understand the risk, and that investment in the area will save the business money in the long run. This article looks at one of the most effective methods of demonstrating the danger of human error to businesses: simulated phishing.
Exposing the human risk: 16% compromise rate
We at usecure work with a number of IT Managed Service Providers. From our discussions with them, we are well aware of the difficulty in convincing some business leaders of the danger that cyber crime and human error especially pose. When management has a "won’t happen to us" attitude, it can feel almost impossible to convince them that cyber crime is a real risk to their business before they fall victim themselves.
This is where simulated phishing comes in: it demonstrates the vulnerability of each individual business and their workforce to cyber crime in a way that no other method can.
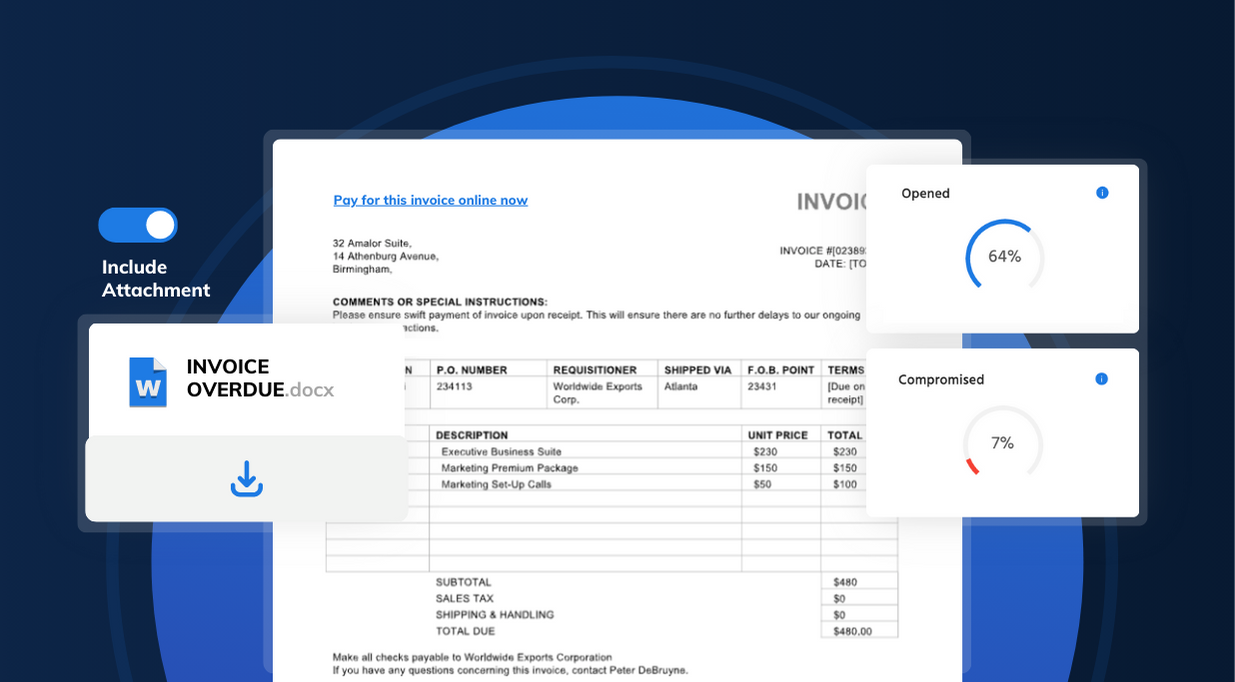
A phishing simulation tests user vulnerability to phishing. Simulated phishing emails emulating real phishing messages are sent to end users, and their reaction to them is tracked and reported. Statistics like open rate (how many end users open the email) and compromise rate (how many users actually give up their details) are essential to find out just how vulnerable an organisation's workforce is to phishing scams.
For more information on everything phishing, read our full guide: What is a Phishing Email?
The results
We measured the success of phishing simulations that our MSP partners sent out in 2019 to their customers. The first phishing simulation that MSPs on our platform sent to each of their customers had, on average, a 16% compromise rate.
That means that 16% of employees, on average, fell for the (simulated) phishing scam.
Here are the full results:
| Sent | Opened | Visited | Compromised |
| 100% | 44% | 34% | 16% |
(The results include data from over 400 users and companies in a wide variety of industries).
- Sent means how many simulated phishing messages were sent.
- Opened is the number of times that the simulated phishing email was opened.
- Visited is how many times the link in the phishing email was clicked.
- Compromised is the number of users that gave up their credentials on the landing page of the simulated phishing scam.
Get a free trial of uPhish and see how vulnerable your end users are to phishing scams.
What did the simulated phishing emails look like?
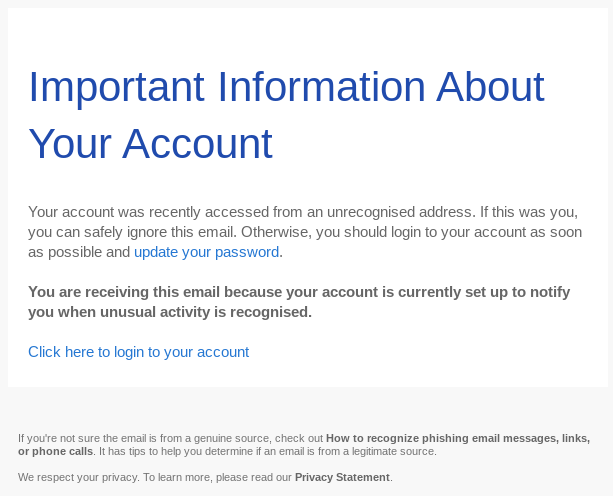
There are many types of phishing attack. Generic template-based attacks that emulate services like Google Drive or Office 365 are widespread, but businesses are also increasingly targeted by highly-customised spear phishing scams. These scams use publicly-accessible information about companies or individuals to make phishing emails that are highly believable to end users.
uPhish, usecure's simulated phishing tool that was used in this study, includes both a library of realistic phishing templates as well as the ability for customers to create their own custom spear-phishing emails. Both types of simulated phishing scam were used in this study.
This is one example of a phishing email used in the study - one based on a generic template:
Why demonstrating the cyber threat to businesses is essential
As long as humans have access to data, systems and devices, they can cause a breach to take place due to error. There is nothing that will entirely remove the chance of this happening, but training your end users to recognise situations where security may be at risk, and to take the necessary precautions to protect their organisation’s computing resources will be essential in mitigating the organisation’s vulnerability to breaches.
While it is essential that businesses utilise the necessary technical measures - such as antivirus, two-factor authentication, and managed patching, the human factor will always leave the company vulnerable unless it is also addressed. Human error can be mitigated most effectively with security awareness training, which teaches end users how to protect the security of systems, data and devices. In addition, simulated phishing emails raise awareness about social engineering, and allow you to measure the risk potential of your end users.
So, how are you ensuring that your end users aren't leaving your business and customers vulnerable?
Want to see how your own end users would fare against a simulated phishing attack? Launch a free phishing simulation with uPhish by following the link below.